Made to de-escalate.Engineered to withstand scrutiny.
Designed for accountability




























Results that make a difference





The BolaWrap is a restraint tool that gives law enforcement and military personnel a way to safely de-escalate difficult situations without causing pain. Instead of using force, it fires a Kevlar cord to wrap around a person’s legs or arms from a distance. This helps prevent injury to everyone involved.
But performance alone was not enough. Agencies also needed a reliable way to track and verify every use of the device. That’s why Wrap asked 28 Gorilla to improve the technology. We engineered every cartridge to capture how it was used, lock that record in place, and help agencies answer hard questions with confidence.
Build trust in every cartridge
BolaWrap is designed to reduce harm. That means it must meet a higher standard of public trust and legal accountability. If a cartridge fails, or if its use cannot be verified, it could raise serious questions during investigations or in court.
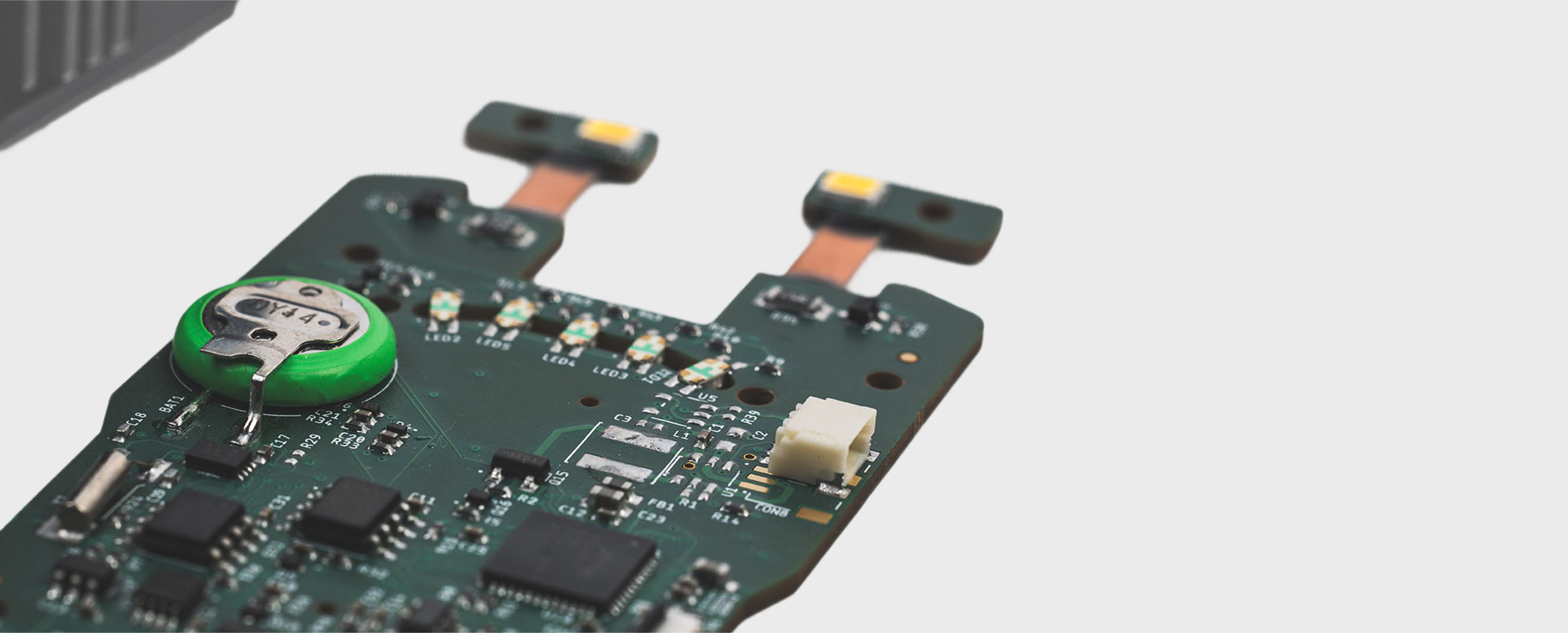
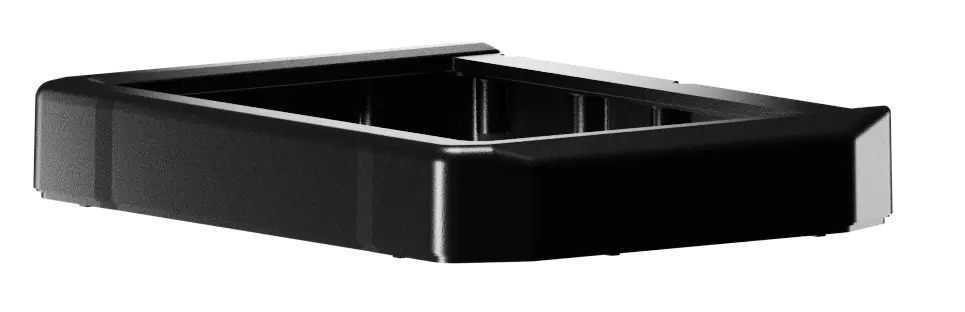
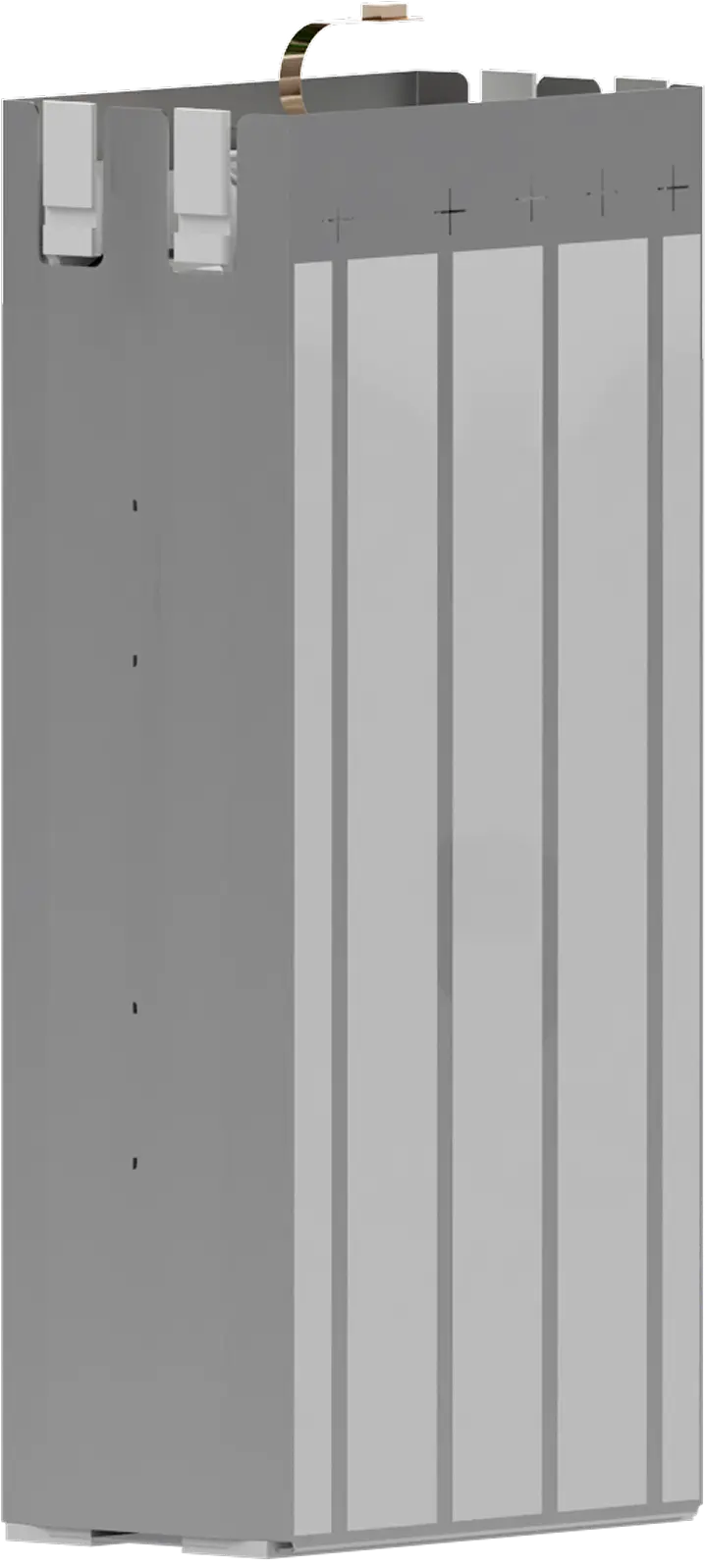
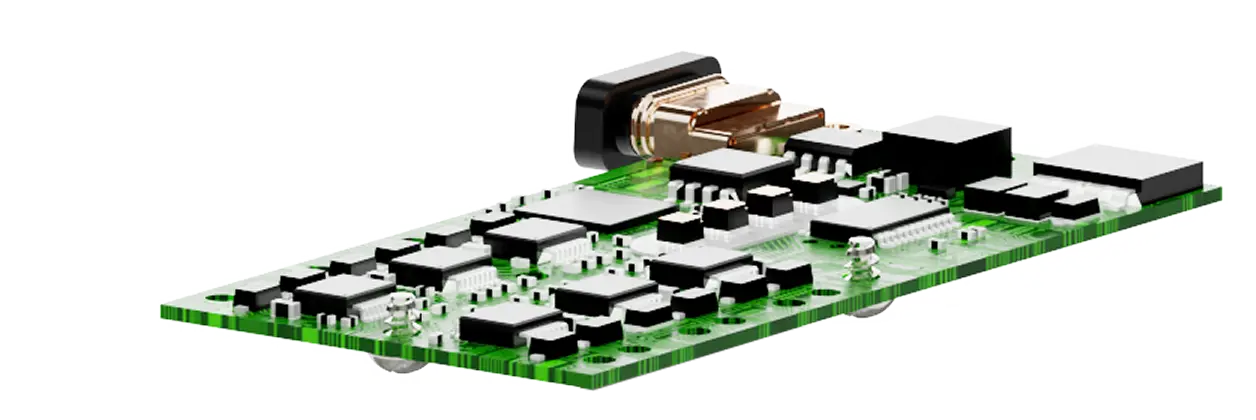
Each sealed cartridge contains the Kevlar cord and internal electronics. Agencies need to know exactly how and when each one was activated. They also need to be confident that the record cannot be altered.
Security from the start
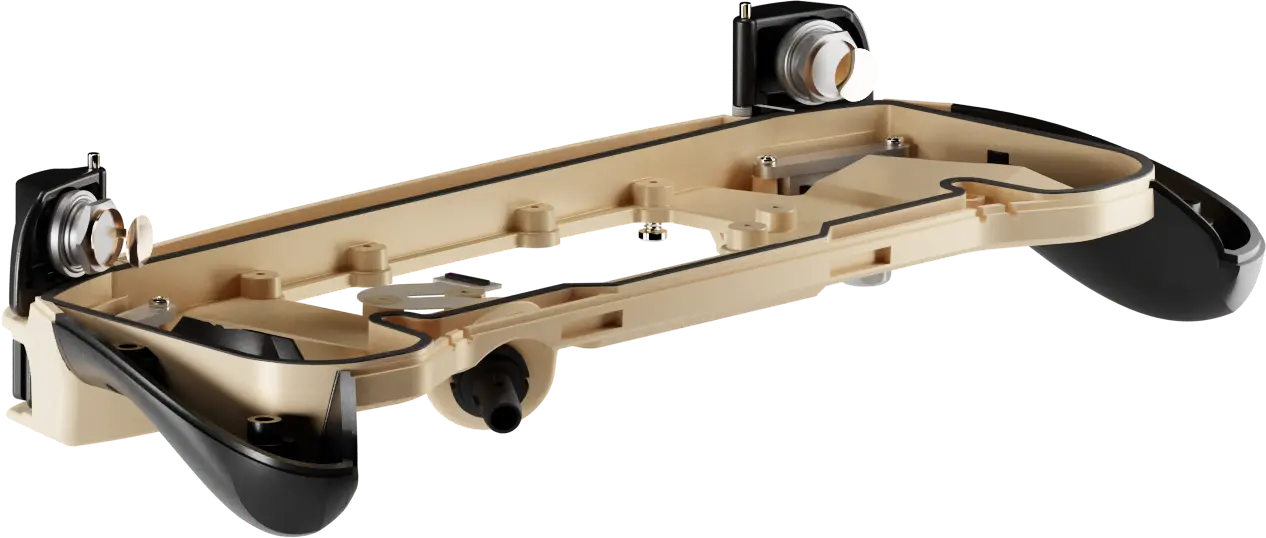
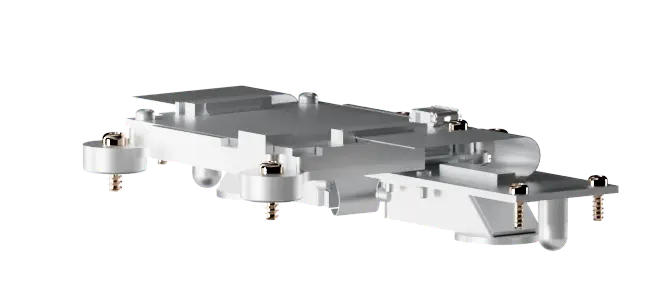
28 Gorilla led the redesign of the cartridge system with three priorities: traceability, security and durability. We added a secure memory chip to record usage data. If someone tampers with the housing or electronics, the cartridge disables itself.
We also redesigned the cartridge housing to make it stronger and harder to manipulate. To support Wrap’s production team, we developed testing and programming tools that verify each cartridge before it leaves the factory.
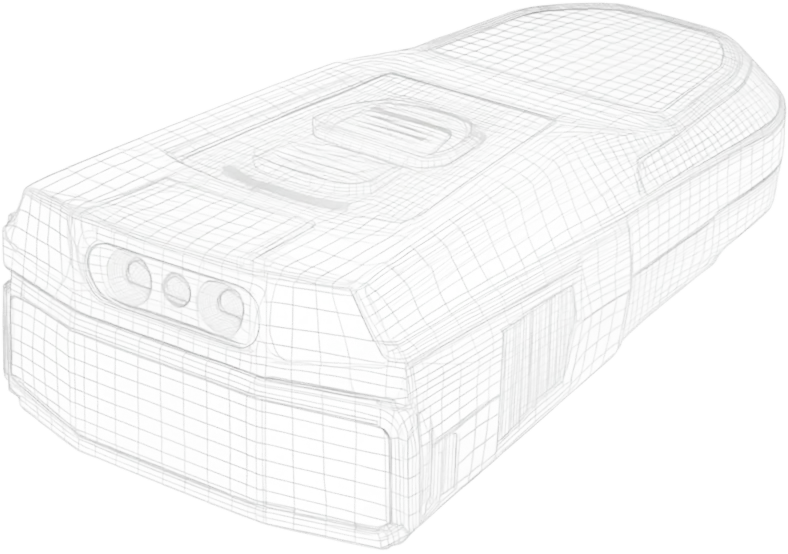
Up close with
BolaWrap
Skills & equipment used


- Traceable electronics design
- Tamper-detection circuitry for regulated environments

- Rugged housing for field conditions
- Impact and environmental validation (e.g., thermal testing, salt fog, EMI)

- Embedded usage logging
- Secure memory for post-deployment verification

- Programming tools for secure systems and traceability
- Factory-level authentication for production verification